Living Dangerously: CCAV 2.0 Beta
While I recommended Kaspersky Security Cloud Free to everyone—wife and friends included—as a much better choice than Kaspersky Free Antivirus (for it’s much more customizable), I don’t use it anymore on my laptop. For some reason, it slows down the moving of large files, despite being configured not to scan archives and installation packages. Either way, both products (KSC Free and KFA) are quite decent and much improved over the initial release of KFA, which only included signature-based detection. In the meantime they’ve both added System Watcher (which includes the detection of malicious activities and of ransomware), although Application Control (which adds an extra layer of protection) is only available in the paid editions.
While shopping around (as a way of speaking), I’ve tested Avast Premier, for two main reasons: the Sandbox and the Anti-Ransomware dedicated protection, with configured folders and all. It wasn’t that bad per se, but it proved to be too aggressive for my taste. There’s however one reason for which I’ll probably never settle for Avast or AVG: some of their detections are not true detections, as both harmless false positives (e.g. keygens) and lethal ransomware can get “Win32:Malware-gen” for a name (the same way Panda does with “Trj/CI.A”). This is not a good management of their product; and when notified in their forum, Avast replied that they don’t support the use of illegal or unethical software (i.e. keygens and cracks), so they won’t whitelist any such thing; OK, but how about reclassifying those ransomwares that were giving generic names?
I won’t mention other AV products that I’ve tested or I’ve skipped the revisiting for various reasons (MBAM for it blocks too many websites and for being blatantly stupid; Bitdefender for its huge RAM usage, something like 600…800 MB in the latest version); I’ll mention however how I started my renewed love affair with the infamously buggy COMODO: by trying Comodo Internet Security (CIS includes everything that CAV and CFW have)!
Yes, CIS is a PITA. Those who have ever heard of cruelsister should already know that she advocates CFW (properly configured!) and nothing else. She doesn’t believe in signature-based detections (neither do I), and often HIPS can’t cope with 0-day malware.
Of course, to keep Windows happy (and Windows Defender inactive), one should use a “traditional” AV that uses signatures. But that’s not the reason I couldn’t settle for CFW alone. I still wanted some signature-based detections, even if they wouldn’t catch e.g. a 0-day ransomware.
Testing CIS–for the whole shebang–was rather painful. I almost forgot how intrusive it can be, not to mention the semantically uninformative if not stupid security profiles (Internet Security, Proactive Security, Firewall Security)! Eventually, I had to uninstall it when it insisted on looking in the cloud not only for file ratings but also for some signature-based detections even with all the modules disabled! (Maybe I should have looked deeper in the settings, but I had disabled everything from the systray icon menu, and it wasn’t enough to keep it quiet.)
Then, out of the blue, I found about Comodo Cloud Antivirus v2.0.470195.867 Beta (the stable version of CCAV being still 1.21.465847.842), which (why is that?!) doesn’t seem to be mentioned in Comodo’s own forums (was it meant to be a closed beta?). So I had to try it…
…and I’m still with it!
I happen to like the new UI:
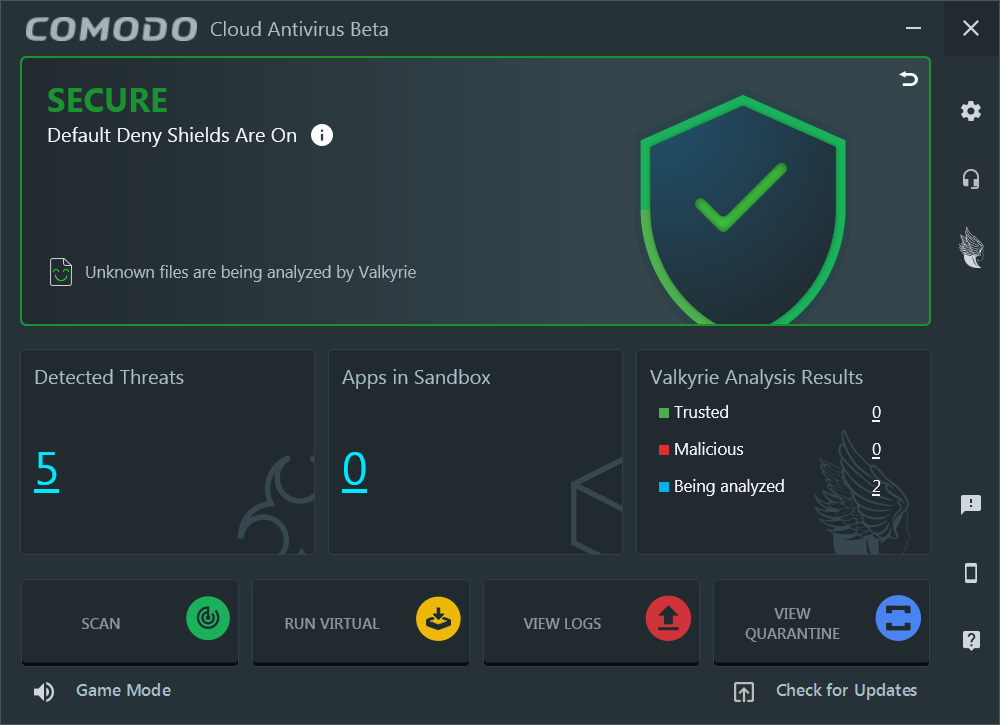
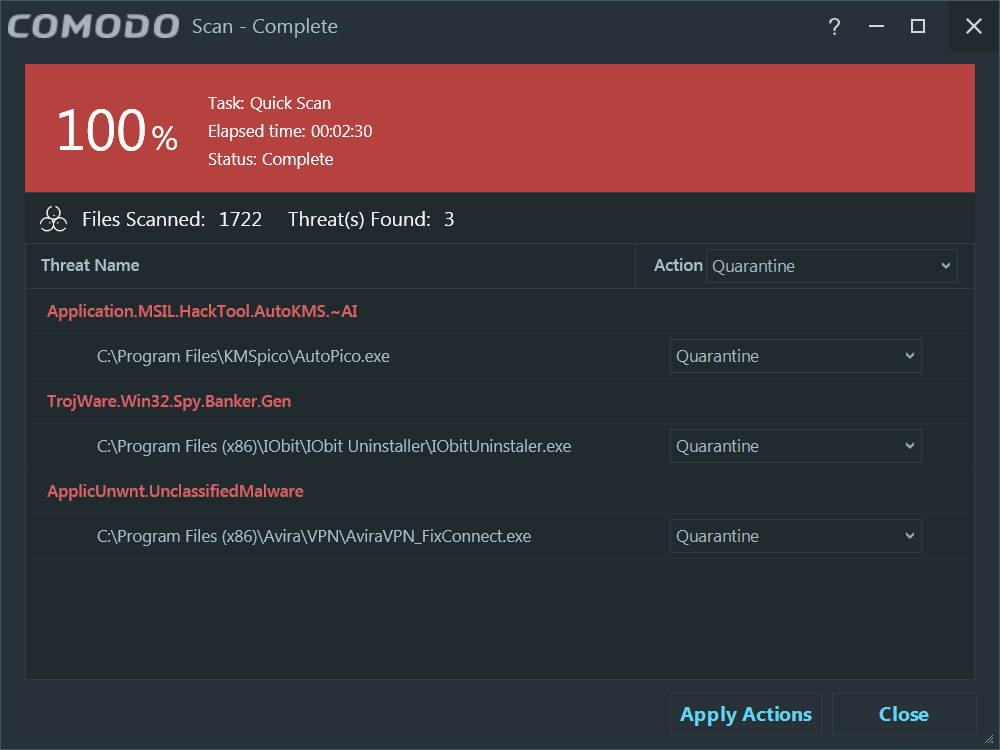
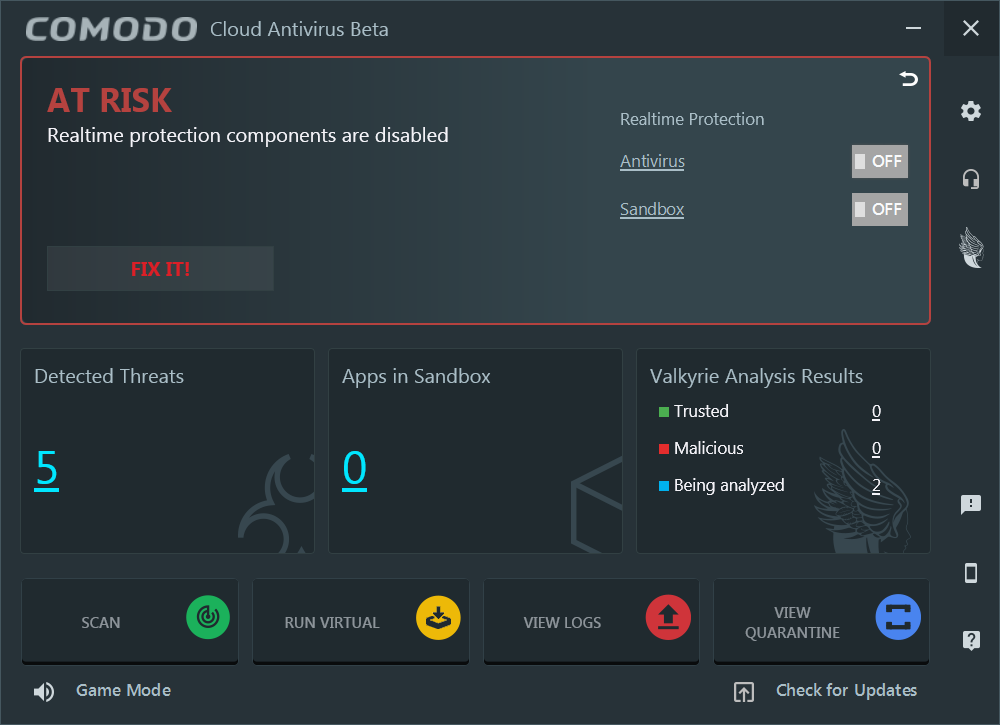
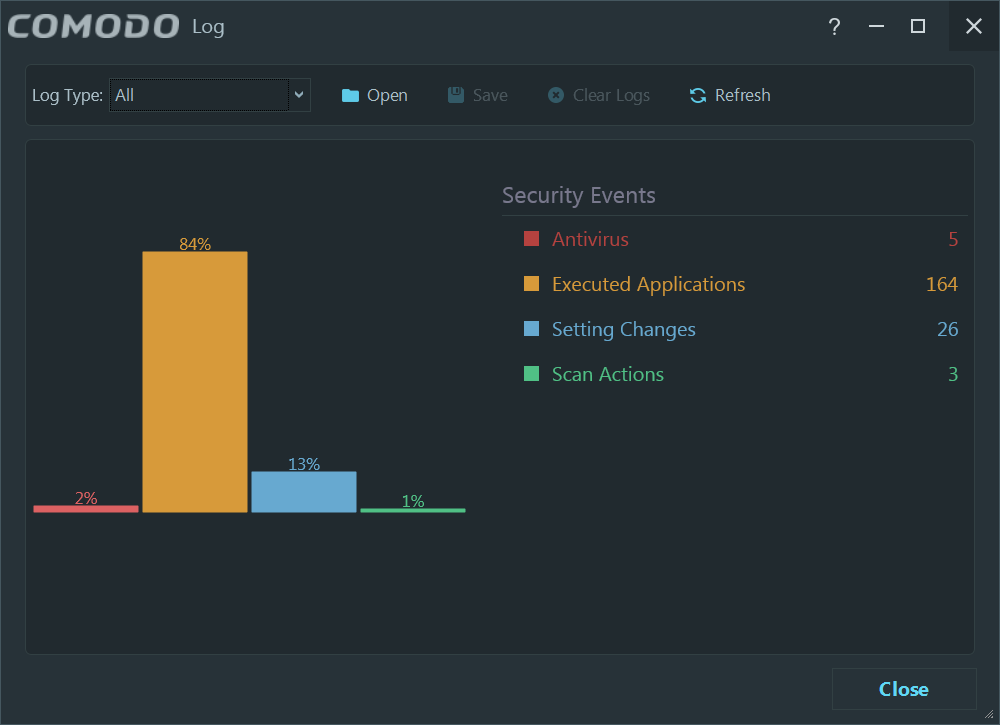
The detections allow you to ignore and whitelist…
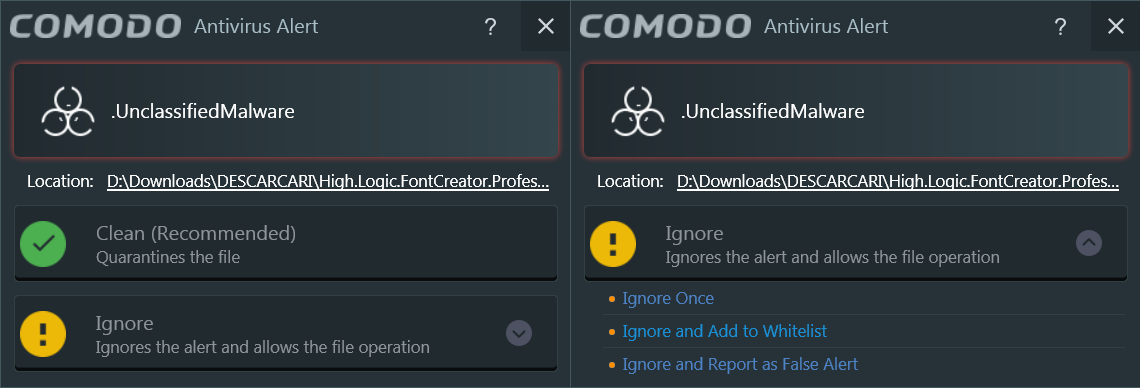
…while the unknown binaries (which are going to be quite a lot for people who install a lot of programs!) are by default sandboxed, but the user is asked first:
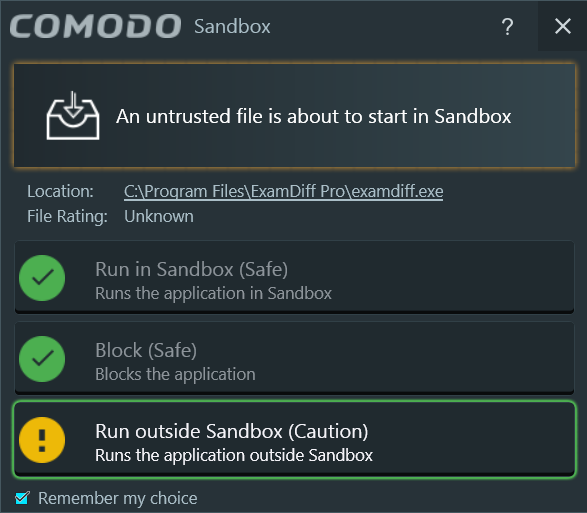
That’s the “deny all by default policy”–don’t allow unknown binaries to run on the unconstrained system!
Traditionally, the sandbox in CCAV was less configurable than in CFW/CAV/CIS, but CCAV 2 Beta comes with a fully configurable beast:
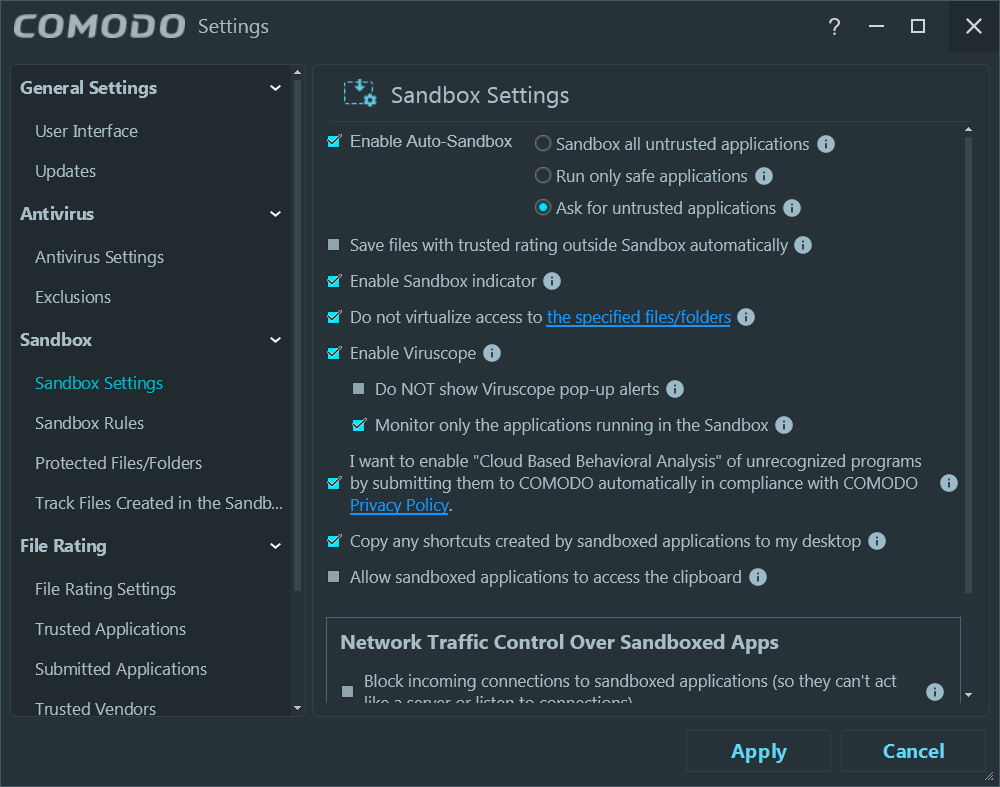

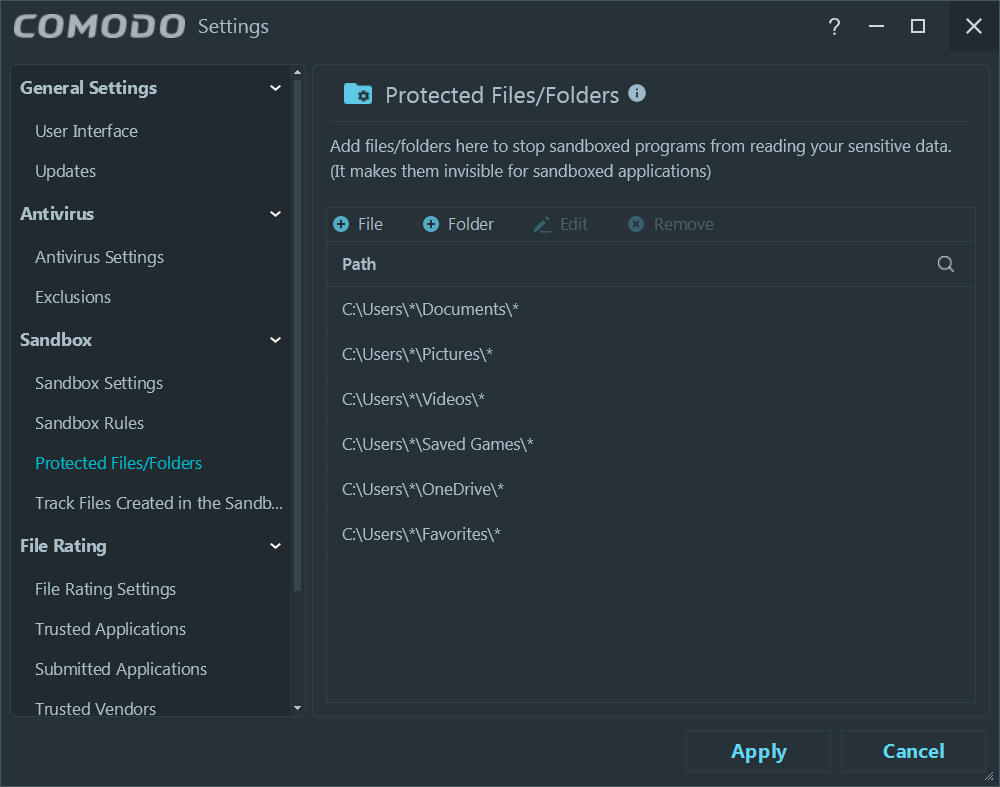
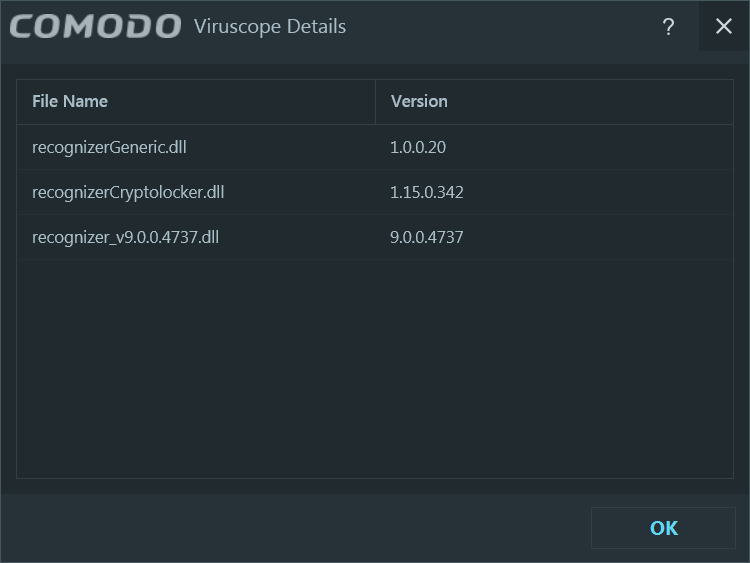
The protected folders are with regards to the Sandbox; there’s no ransomware-specific protection à la Trend Micro or Avast (paid). Speaking of ransomware, I’m not sure what their “Cryptolocker recognizer” does:
One can add trusted applications to File Rating:
Interestingly, it includes two features that in the rest of the Comodo line of products are under “HIPS Settings”:
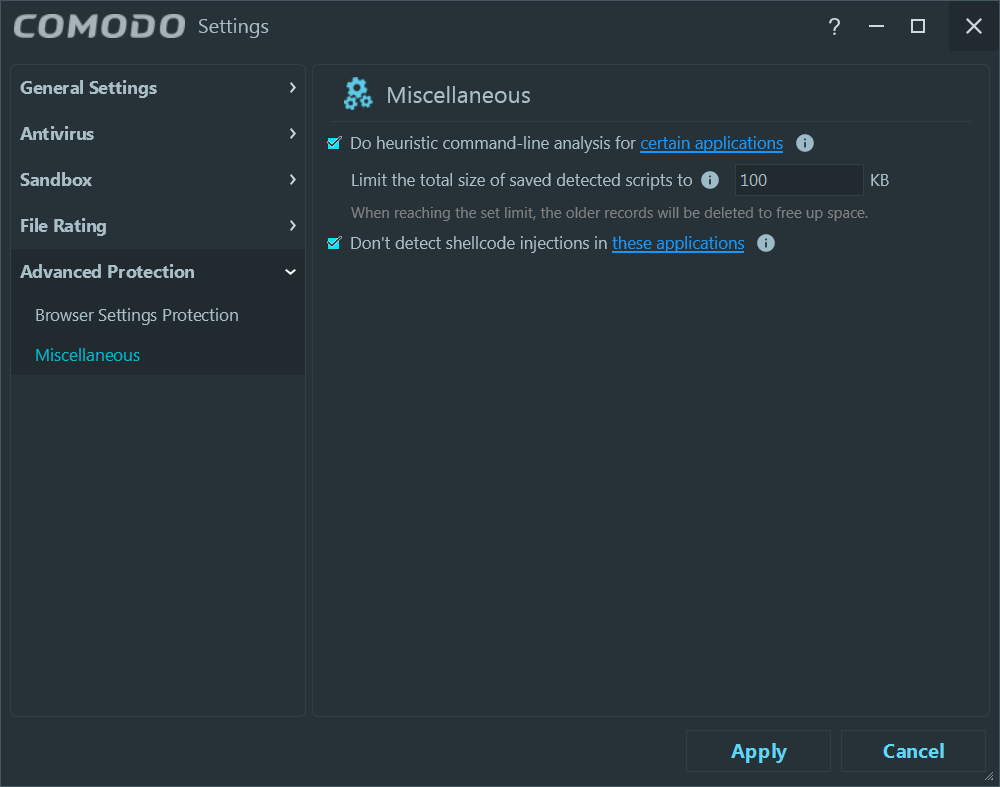
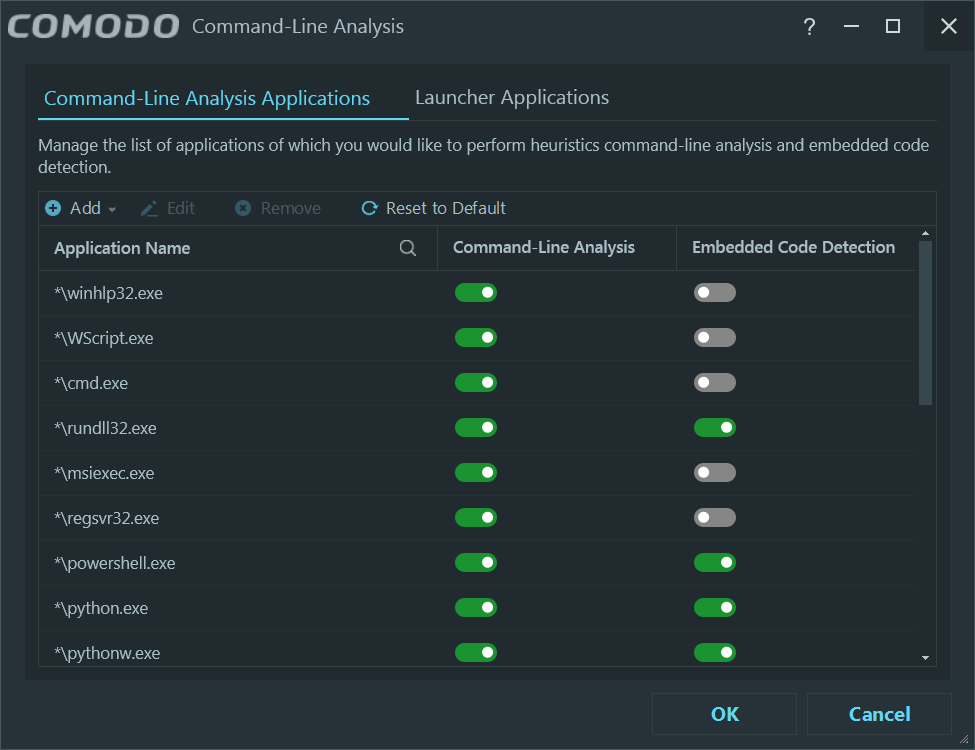
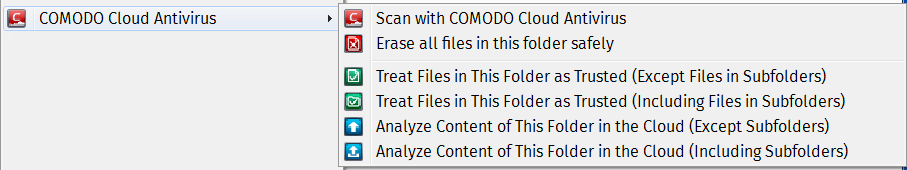
Finally, the contextual menu is quite nice too:
What’s my actual experience with the beast? Consider that I have 205 installed programs!
Well, on the first launching of a binary, it could take up to 2.5 seconds (by default) to be analyzed in the cloud; if it doesn’t know it, Valkyrie’s going to hear about that; and the user will be asked to run the binary in the Sandbox. By telling CCAV to remember to run the respective binary non-sandboxed, the binary will got whitelisted and added to Trusted Applications.
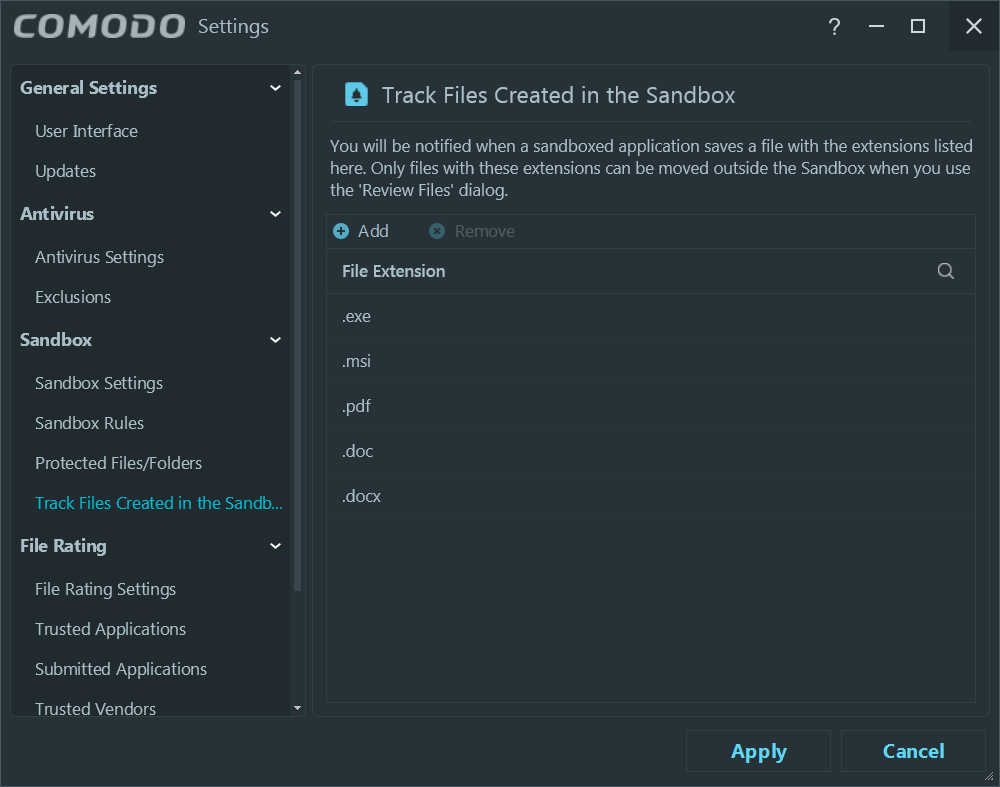
I never run any browser in the Sandbox, especially as I want to save the files in the actual filesystem, but based on the “Track Files Created in the Sandbox” settings, those files can be moved out of the box.
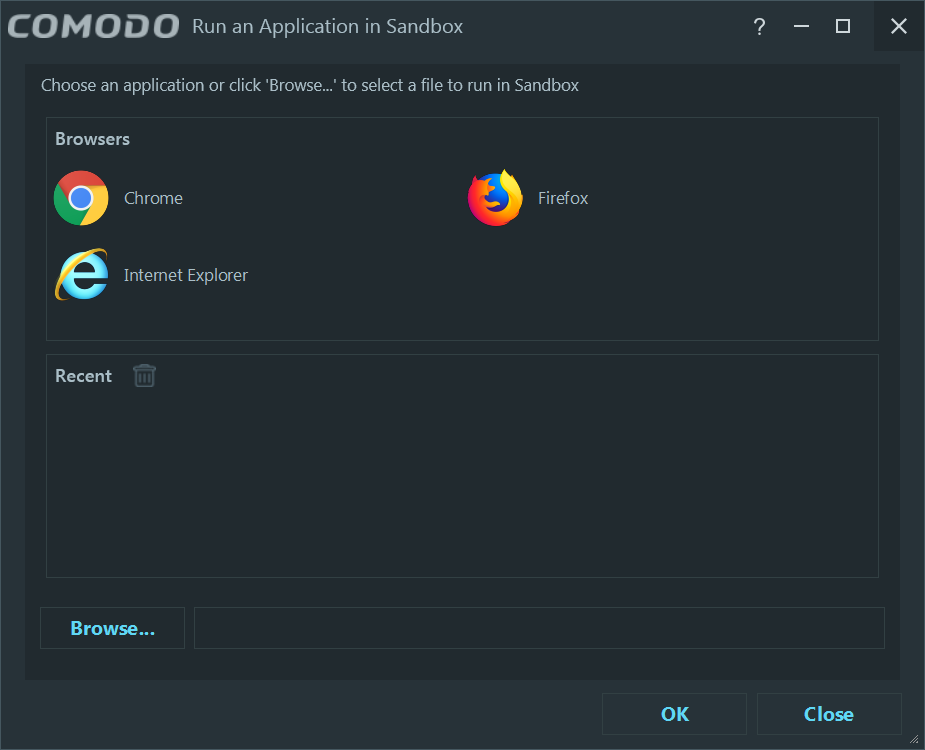
Not my cuppa tea, as I could be saving files weighing 2 GB each!
Now, how to get a better protected system, knowing that Comodo’s signatures are weak, and that the temptation to run an unknown binary out of the Sandbox is huge?
First, having anything new tested by VirusTotal. False positives can be identified by Kaspersky detecting them as “not-a-virus:something” or by some other product including hack, crack, or patch in the detection name.
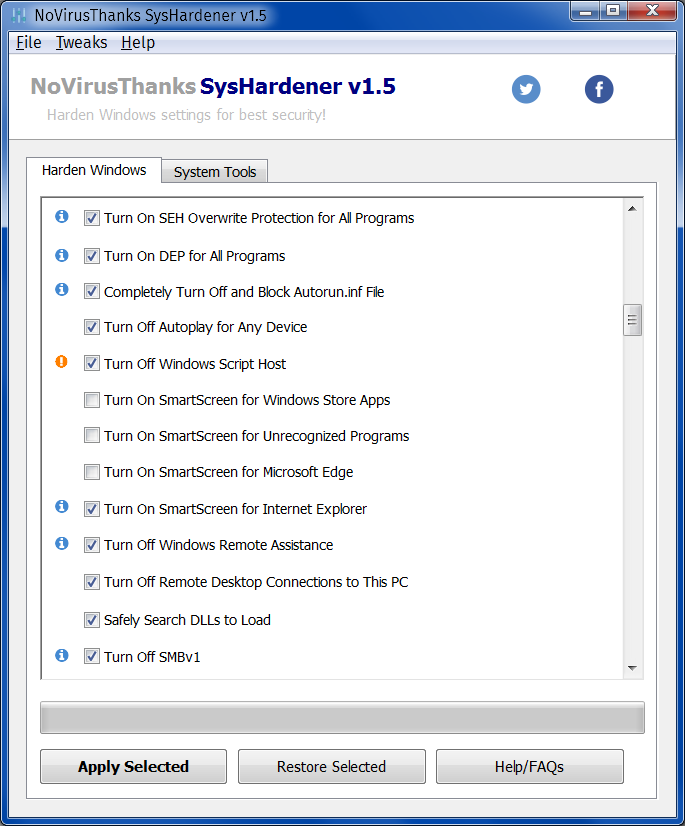
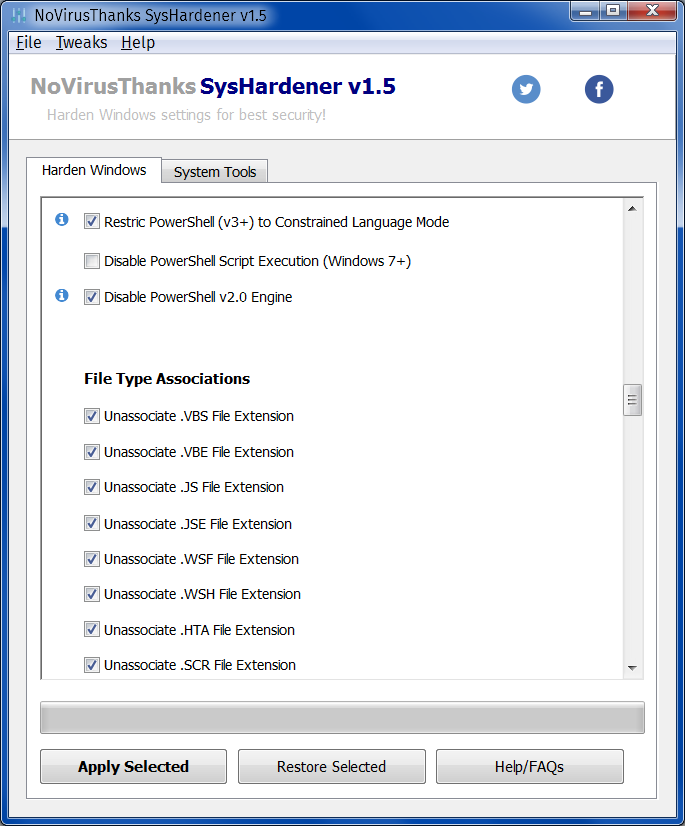
Secondly, harden the system using SysHardener. It’s a static protection that only disables or enables various system features:
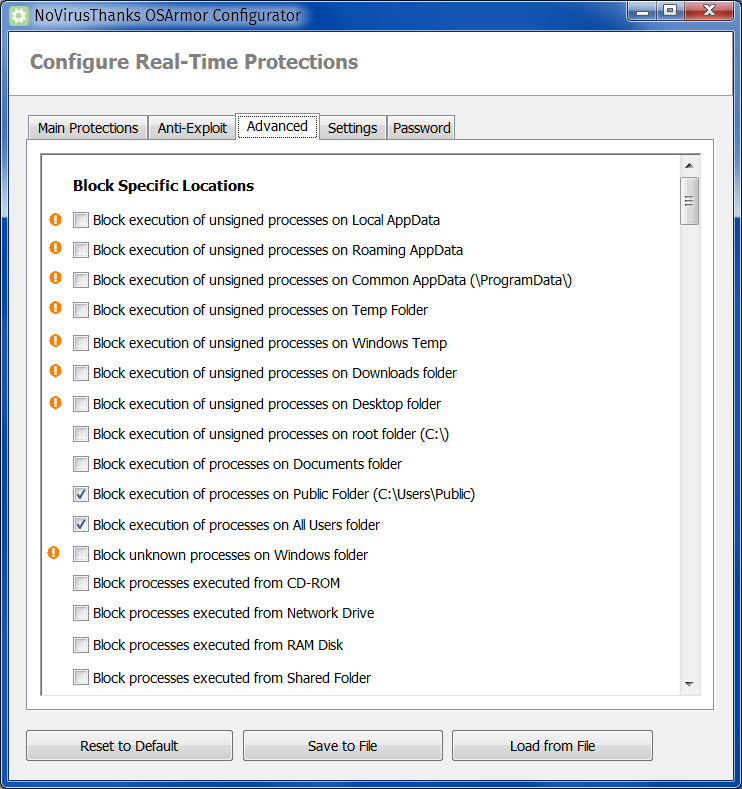
Thirdly, add OSArmor, a resident protection that allows a much better lock-in of the system:
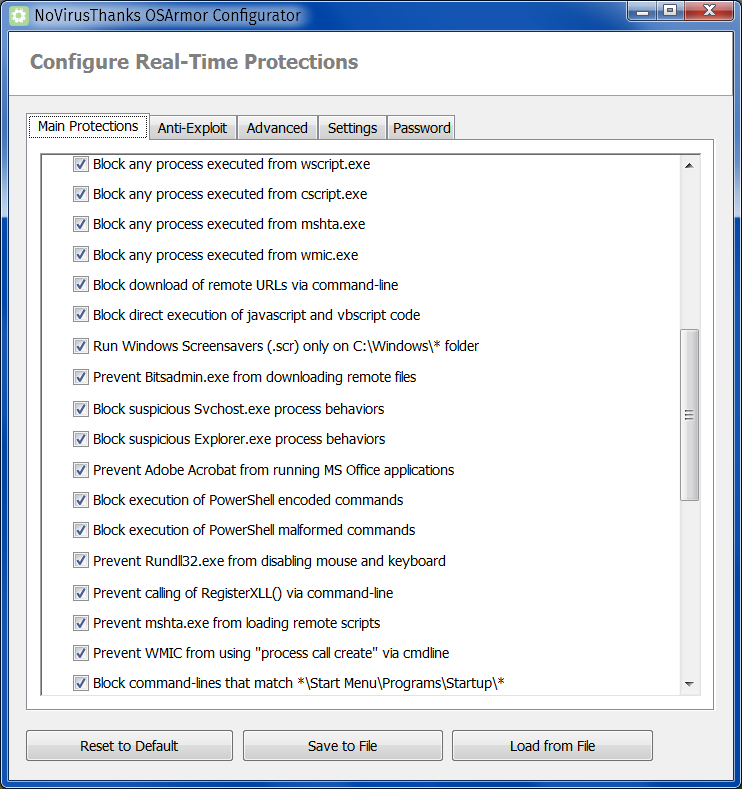
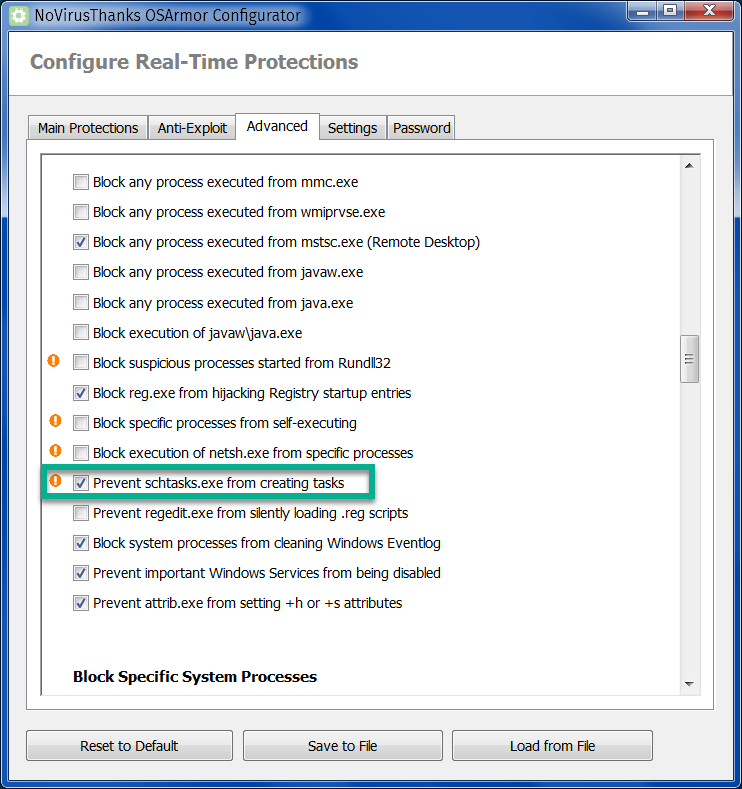
The highlighted item is very useful to those who–like me–hate when scheduled tasks are created by an installer (or a malware!) without asking the user first.
I forgot to mention one more thing I like in my security setup (which is not convenient for everyone though): there’s no stupid browser add-on to forbid me to visit a URL. I never believe in blocking URLs (or entire websites, as it’s too often the case with those stupid blacklists). I want to to be able to visit whatever I want and to download no matter what I want; only after a file is downloaded I accept to have it scanned, and blocked from execution (especially when not sandboxed!) until I explicitly agree to run it! Excuse my French, but URL blocking is a thing designed by idiots for the morons.
UPDATE: For the sake of having an addition that claims to deal specifically with ransomware, the Kaspersky Anti-Ransomware Tool for Business is now at version 4.0.0.861, released on February 21, 2019. Here’s a direct D/L on comss.ru.
Not that it would be a way to actually see it in action. But it’s there.
It claims to also detect some malware (KSN-based, I guess). Otherwise, it’s an upsell attempt for a full Kaspersky suite (this tool doesn’t have a Premium edition, they mean a paid product like Endpoint Security, Small Security Office, KIS or KSC):
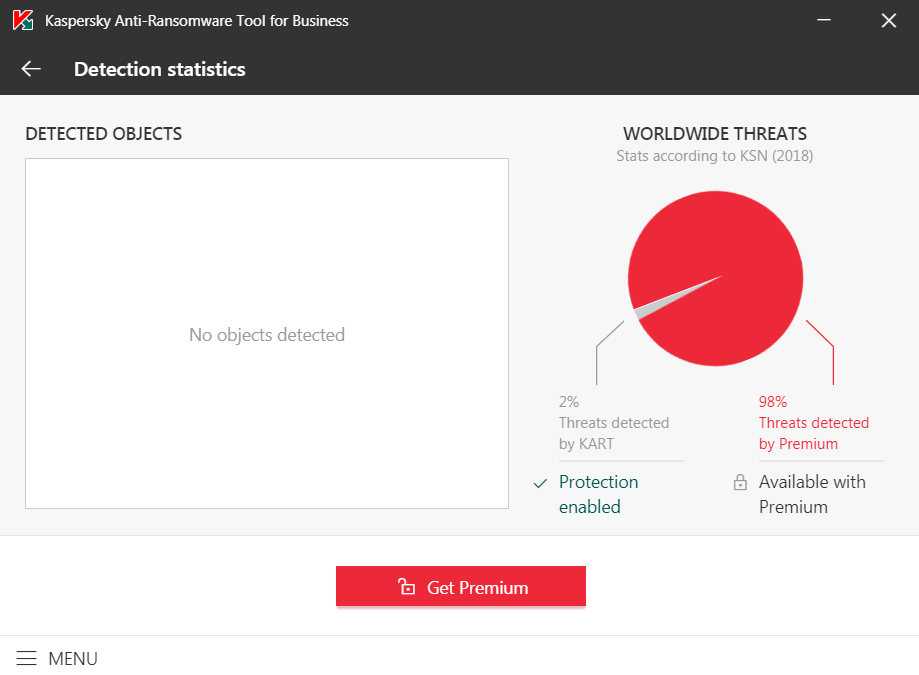
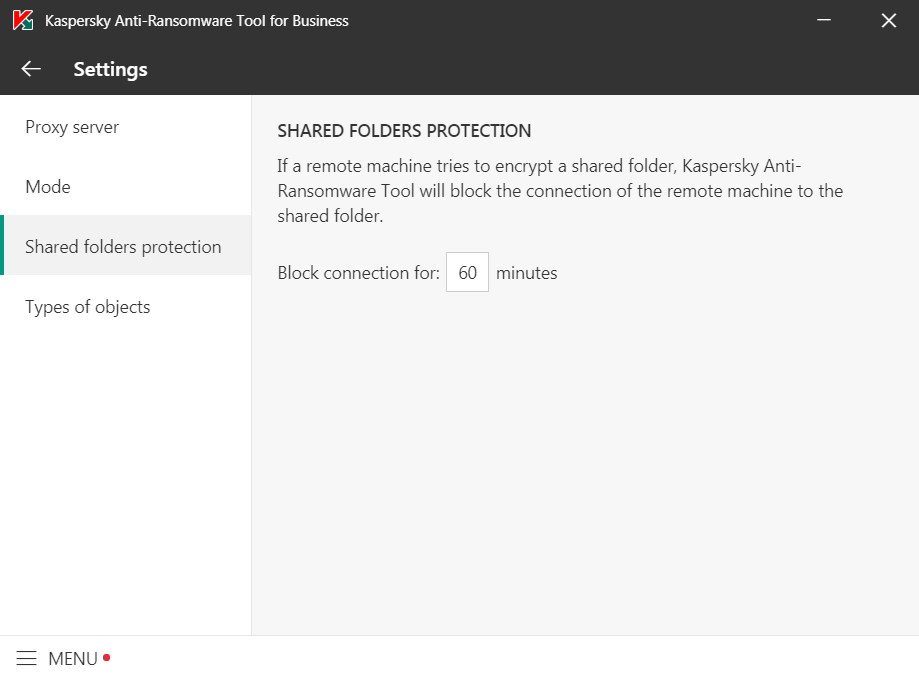
Nice try, Yevgeny. You’d better tell your people that if a remote machine is infected by ransomware, blocking it for 60 minutes is dumb. It should be blocked forever, unless or until it’s manually unblocked!
LATE EDIT: Knowing that Comodo Internet Security Premium 11 got perfect protection scores in AV-TEST’s Product Review and Certification Reports for Nov-Dec/2018, Sep-Oct/2018, Jul-Aug/2018, I suppose CIS deserves a second chance, but I just felt it was too annoying as I tested it. How about a beta of the next version, 12.0? It exists (see here and here), but there are some caveats:
- The Autosandbox still means that it will not ask before sandboxing! CCAV 2.0 Beta, while having a “default deny” policy, always asks before sandboxing.
- In order to install the online setups (those 5.3 MB ones), one has to modify the hosts file; then those changes have to be reverted to be able to receive signature updates. (There’s however a full setup.)
- Many users have reported for this 12.0.0.6798 version serious troubles with HIPS, which tends to warn about virtually every single application! Not only this means too many exceptions need to be added, but a Win10 the system might get unresponsive to the point that even a reboot request would be ignored! The system actually slows down very much (it will eventually reboot… eventually).
- Some people failed to install it on Win7 or Win8.1.
- After closing a sandboxed program, there might be “leftovers” in the Task Manager, even after the Container has been reset.
That’s too bad, considering that CIS 12 Beta comes with a few improvements over CIS 11 (e.g. full Windows 10 version 1809 support; extended containment/sandbox rules; “Heuristic Command-Line Analysis” and “Embedded Code Detection” for scanning and monitoring of auto-run entries; Powershell_ISE analysis; updated AV engine), and a number of fixes. I don’t know though whether it fixes or not an issue that is most annoying when it happens: CIS 11 can randomly decide to block, contain or quarantine an application, despite having it set as trusted, or added as an exclusion! (This is what made me stop using Trend Micro; this and Trend’s lack of a true quarantine management.)
Oh, as for the non-beta version of CCAV (1.21), it looks like its sandbox is as configurable as the one in CCAV 2 Beta, and here’s a full review from January.
UPDATE: Comodo Internet Security 2019 (v12.0.0.6810) is out of beta. For those brave at heart 🙂

A few of the many interesting things revealed by Fabian Wosar, head of research at Emsisoft, in a Q&A tread on MalwareTips:
___
Q: «…you often see that attackers don’t use classic malware at all. Everything is done through Powershell.» Would this mean is Powershell was restricted or blocked complete would this mitigate malware executing via Powershell?
A: You can just uninstall it if you don’t use it (and most users won’t). That being said, Powershell is a tricky beast. Even if you block the Powershell executable or uninstall it, it is still there in the form of System.Management.Automation.dll for example. There are multiple other applications that parse command lines or configuration using Powershell for whatever reason. Those can be used to run Powershell code even though they have nothing to do with Powershell at all. MsBuild is one of those for example.
___
Q: Does EAM always use the most recent/actual Bitdefender engine and how much performance improvement we can theoretically see if Bitdefender’s engine is removed from EAM?
A: Scan times would be cut on average by 60 – 70%. And yes, we always use the most recent Bitdefender engine. We don’t use the same settings as them though. For example: Bitdefender, like many other AVs as well, has invisible signatures. Think of it as a form of QA. If they are unsure on whether or not a new signature may cause false positives, they release it marked as invisible first. The scan engine then sends back information about all detections triggered by that signature. The server may tell the engine either to upload the file for further analysis, tell the engine to show the detection to the user or tell the engine to not show it. We have this stuff completely disabled as especially the upload stuff we don’t feel particularly comfortable with. However, it also means we will have slightly worse detection rates from the Bitdefender engine as any product that has these features enabled.
___
Q: Do you have in plans to release a free, basic version of EAM just like Kaspersky did? 🙂
A: We may. The problem is, that ultimately with these free AVs you as a user pay with your data. That’s generally speaking something we don’t feel very comfortable with. Especially given that not a lot of people are even aware of it.
Recently I was kind of surprised to see that an otherwise super privacy conscious user had Traffic Light installed for example. It doesn’t seem to be common knowledge that Traffic Light and a bunch of other browser extensions (Comodo Online Security Pro, Norton Safe Web, Avira Browser Safety, Avast Online Security being the biggest ones) like it will literally send every single URL you visit in clear text off to the vendor’s server. The privacy policies aren’t always clear and kinda sketchy at times. I am sure that some people don’t mind. But I am also sure that a lot of people do mind, but simply don’t know.
> a Win10 the system might get unresponsive to the point that even a reboot request would be ignored! The system actually slows down very much (it will eventually reboot… eventually)
My God. This reminds me of the time of my (bad) experience with Comodo … Quite that. An horror, typically Comodo.
Apparently, CCAV is to be considered abandonware. Not only CCAV 2.0 Beta wasn’t ever mentioned officially, but CCAV itself was last updated in Sept. 2018. On Comodo forums, someone (5245 posts, the rank of “Comodo’s Hero”) has an explanation:
As a matter of fact, Umesh was last active on September 07, 2018. His LinkedIn profile shows that his 14½ years at Comodo ended in Sept. 2018, when he moved to Verizon.