The VPN Myth
I’m sick of how many people are still believing that, if they use an open public network without a VPN, their credentials might be stolen. Smart, educated people believe this to be true, despite having been told it’s been years since no connection of relevance is made using insecure protocols. Maybe it’s time for this stupid myth to end.
As it happens, I never watched this video before, yet Tom Scott explained it so well in the fall of 2019:
Make sure you watched the video before going on.
There’s little to be added, except for my summary not of the video, but of what I think on the matter:
- Nobody should use a VPN for the reasons they’ve been told they should use such a product.
- This doesn’t apply to the corporate VPN clients used more and more during these times to connect to a company’s internal network, so that remote work would be possible.
- Nobody should use a VPN based on the “review websites”; they’re known to be anything but competent and professional assessments (more about that, later).
- Nobody should trust claims to the effect that “we don’t store anything”; in most civilized countries they have to store something for some time, and when the traffic is capped they can’t do that without storing for a month when you have connected and how much data you’ve used. What’s important though is that “they” can’t store data that would allow the “copyright infringement Gestapo” to sue you for the movies you’ve downloaded via P2P.
- Nobody should trust a VPN because it’s incorporated on a godforsaken island that’s both a tax haven and a criminal country, simply for not trusting any country that’s part of Five Eyes, Nine Eyes, Fourteen Eyes, or whatever and however you like to count. The purpose of such intelligence alliances is not to spy on your downloading of the latest Academy Awards winner!
Legitimate uses of VPN, beyond the case you’re a terrorist or a pedophile, include:
- Pretending to be in a certain country to access geographically restricted contents. Some people want to access the US versions of Netflix, Hulu, Rakuten, etc.; some others want to access public TV channels from France, Germany, Italy, UK, etc. that cannot be accessed, “for licensing reasons,” outside the respective territory. (There is an EU directive that mandates the implementation of a mechanism that allows license fee payers who are temporarily out of the country to access the public radio and TV stations they paid for; the Belgian RTBF has implemented it, most EU countries did not.)
- Pretending to be in a certain country to access resources that are censored in one’s location. No, this is not about China. Many US websites are unavailable to EU viewers, because of the GDPR. Gutenberg.org is unavailable in Germany. Courts in countries such as the UK, Italy, France, Germany, Romania have ordered ISPs to block access to some websites considered to be containing contents that are “illegal” in some way or another. Zippyshare refuses to serve connections coming from most Western European countries. Etc. etc.
- Pretending to be in a certain country to get contents as seen by people in that country. Not only Google tailors its results depending on your IP! (We’re not discussing “search engines that don’t track you, but that still give results depending on your location, such as the overrated DuckDuckGo,” nor the way Google, YouTube and other sites give different results depending on your being logged in or not. Also, let’s ignore for now that Bing does respect the target country, e.g. bing.fr or bing.com/?cc=fr doesn’t show the same contents as bing.co.uk or bing.com/?cc=gb). Sometimes you just want to “be” in another country! Virtually, that is.
- Avoiding the “copyright infringement Gestapo” when you download torrents or contents using any kind of P2P protocol. Law, justice, and ethics are three entirely different things. Not all the laws are ethical and just, and even when they are, sometimes they defend unfair business practices. Say I paid a French paperback €17.99, and I’d like to have a digital version of the same book. How is this right to ask something like €14.99 for an ePub instead of something more like €5.99? Once you have the document that was used to print the book, making an e-book has infinitesimal costs. Even the “stealing” of digital contents is overrated: when you “steal” a ripped CD-ROM, you don’t steal the cover price of the CD. When you steal 2,000 books or 100 movies you don’t create a “missed business opportunity” equal to the list price of those products. When forced to purchase them, most people would probably buy not more than 1% to 5% of what they “stole”; and let’s not forget that those who steal from everybody are those Mafia-like organizations called RIAA, MPAA, and the equivalent associations in other countries (e.g. GEMA and GVU in Germany, SACEM in France) who lobbied for laws that added a “blank media levy” and a “private copy levy” on blank CD-ROMs, DVD-ROMs and Blu-ray discs, on HDDs, SDDs, SD cards and USB flash drives, on smartphones and tablets, based on the “presumption of guilt” that’s contrary to the idea of justice! They “assume” the user will break the law and “steal” from their clients, so they charge everyone a lump sum, which however doesn’t give anyone the right to “steal” Intellectual Property! Even in 2021, supposing you want to purchase a flash drive as small as 8 GB, its price would include a “statutory €1.20 GEMA fee” in Germany! Purchasing a smartphone in France means you’re paying “for your criminal mind”: €10 if the storage is 16-32 GB, €12 for 32-64 GB, €14 for >64 GB; USB flash drives and SD cards are charged between €1 (up to 8 GB) and €4.60 (>256 GB); HDDs are charged €6 to €15 in France. The more the country you live in is considered “democratic,” the more they steal from you, and they consider you “criminal by default.” So how is one supposed not to take revenge? And how about they prove what they do with this extorsion money? As long as such organizations cannot possibly know how much each content creator has been affected by the “illegal” copies, the respective artists cannot be justly compensated, and your money is simply pocketed by these organizations, or they’re used to increase the pay of some major names, to the detriment of the niche ones and the indies.
- Quickly getting a different IP, should you need to avoid waiting on those download sites that insert a waiting time between subsequent downloads, this delay being forced not via cookies, but based on your IP.
- Some people also prefer to use a VPN to avoid the need to use ad-blockers, firewalls, and the like, should their preferred VPN be offering such privacy, security, and convenience features. This shouldn’t be the main reason to use a VPN, though.
Some more insights from 2019: do you like any of CyberGhost, IPVanish, PureVPN, Hotspot Shield, NordVPN, ExpressVPN? Read Shattering the Grand Illusion of Cookie Flavored Lies. (ProtonVPN isn’t analyzed in the article.) OK, this is about their websites, not about their VPNs, but still, it shows to which extent they’re like Facebook, and you’re a sucker.
And here’s a nice article on Windscribe’s blog: We’re not paying for #1: not only Yegor explains why they don’t pay for reviews, but he also reveals the industry context:
These days, however, many tech companies prefer rapid growth over monetization. This effectively forces companies to raise millions or billions of dollars in order to keep operating at a loss. You heard correctly, they make negative money, sometimes for years or decades on end! Eventually the money runs out, and companies are forced to think about what they should have been thinking about from the very beginning: “How do we pay for everything?” You know what else desserts and high fives don’t pay for? Needlessly large 60,000 sq ft. open-concept offices, Juiceros, and in-house prostate massages, oh, and most importantly investor ROI. So what do they do when they cannot pay their investors back? They begin to monetize your data and trade it like currency. Facebook is a classic example of this (special thanks for screwing up Oculus and Whatsapp!).
Sadly, one of the few ways VPN companies can compete in this market is through advertising. And where there are ads, there’s tracking. These trackers are used to optimize sales funnels and improve the efficiency of ads — ironically, the exact same things that VPN companies are supposed to protect you against. Is this hypocritical? Yep. Do all VPN companies mean you harm? Nope. Even ethical VPN companies can fall into this trap, and it is highly unfortunate that the game tries to force everyone to play dirty in order to succeed. If you don’t believe us, visit popular VPN websites and check to see how many trackers you are bombarded with (then compare it to ours).
Now, to the reviews:
The original concept of affiliate programs was good: find an expert in a field that has built a legitimate following, have them review and/or recommend a product, and then give them a cut of the profits generated from the sales of said product (a.k.a. kickbacks). In a perfect world, this is a pretty ethical practice. We trust those that demonstrate trustworthiness, and we trust those that we feel have our best interest in mind.
Sadly, in this day and age, everyone is a self-proclaimed expert. The standards for what people consider to be an expert are lower than the worker age limits at an iPhone factory; all you really need is an SEO-optimized WordPress site. In most other industries this isn’t a big deal since your safety isn’t threatened by which brand of coffee or phone case you purchase. However, when it comes to VPNs, choosing the wrong one could lead to serious real-life consequences.
Unfortunately, many “security blogs” and VPN “review” sites are not operated by experts at all. Rather, by marketing companies specializing in advertising and SEO for their own customers, who then chose to dabble in VPN reviews as a lucrative side gig. Even the reviews themselves are written by outsourced bloggers. You’ve probably seen countless “Best VPN for [insert topic here] in [insert year here]” articles. Most of the time the articles aren’t giving you any new or relevant information, they just have the right keywords to rank well. Take this example of the highest-rated Chrome “privacy” extension. It quite literally doesn’t even proxy any traffic, and is useless on its own. Or this page, that ranks free VPNs, with #1 option being a paid-only VPN. The only objective of these articles is to rank VPNs in a very specific order to funnel people to the “top-ranked” providers.
I bet you won’t like this part:
Look, we’re no angels either, at least when it came to promotion. When we first launched Windscribe back in 2016, we also participated in these “bidding wars”. Shortly thereafter, we saw the futility of our ways. The only winners in these bidding wars are the sites that perpetuate the deceptive practices in the first place. In order for Windscribe to receive a high ranking with some of these companies, they would ask us for $50 or more per CPA to make it “worth their time”. Guess who ends up having to absorb the majority of that cost? You do. This is why VPN service prices in the last 10 years have remained unchanged for the most part, while the price of bandwidth and cost of computation continues to drop. The increasingly bigger profit margin ends up in the pockets of these marketing sites and advertisers.
I won’t pretend to be giving a white check to Windscribe, but here’s the context for me:
- I liked NordVPN, despite their reliability being variable in time. Currently, I don’t have any license with them, and I don’t intend to trust them anymore. I should probably pay a visit to their HQ in Panama, or to their offices in Lithuania and Cyprus, to complain. Not. By the way, the server you’re connecting to (and which then redirects you to another country) most definitely cannot be in Panama, so the entire hype about “Panama doesn’t have mandatory data retention laws” is pure bullshit.
- I can’t be made to trust ExpressVPN, after having read too many overpraising reviews about them. Too good to be true. The British Virgin Islands are British only in name, as they have a completely separate legislation (more distinct than, say, that of the Channel Islands or of the Isle of Man). They’re not in the “anti-money laundering and counter-terrorist financing deficiency list (FATF AML),” but the US Department of State considers them as High Risk (“Primary Concern”), and they only joined the fight against money laundering on Sept. 22, 2020. I suppose that’s a good reason to put your money there, right?
- ProtonVPN couldn’t convince me. It’s nice that they have a free option with servers in three countries, and it’s understandable that such servers are offering under-average performance, but we simply didn’t click.
On the other hand:
- Windscribe can help in an emergency, by offering for an e-mail account 10 GB/month for free, with a choice of servers in 10 countries (US, CA, UK, HK, FR, DE, NL, CH, NO, RO), compared to 63 countries in the paid version.
- Windscribe’s Yegor explained Windscribe’s logging in detail. It does make a lot of sense, technically. (They also detect accounts that are shared with the entire planet, which is something that others do too; lately, even NordVPN started to do that.)
- Windscribe’s plans seem reasonable enough, $9/month or $49/year, and they even offer fully customizable data plans in which you add countries to the free plan: “Each one is $1 per month and adds 10 GB on top of your allowed monthly bandwidth. $2 minimum.” I didn’t check for possible resellers at a discount (they might not exist).
- Windscribe don’t offer on their website “62% off” or “75% off” temporary discounts “only valid for the next 23:59:59” or “for the next 59 minutes 59 seconds” or some similar shit, as some big names do.
- Windscribe supports Windows, Mac, Linux, browsers, smartphones, tablets, smart TVs, routers.
I do have some criticism for their Linux page. Debian 10 is OK, Fedora 22+ is meant to include 34 (noticed the plus?), CentOS 6+ is fine, but Ubuntu stops at 19.04, which isn’t even an LTS distro. However, I tried it “the orthodox way,” meaning by adding the repository, not just getting a .deb file, and… it just worked in Ubuntu MATE 21.04!
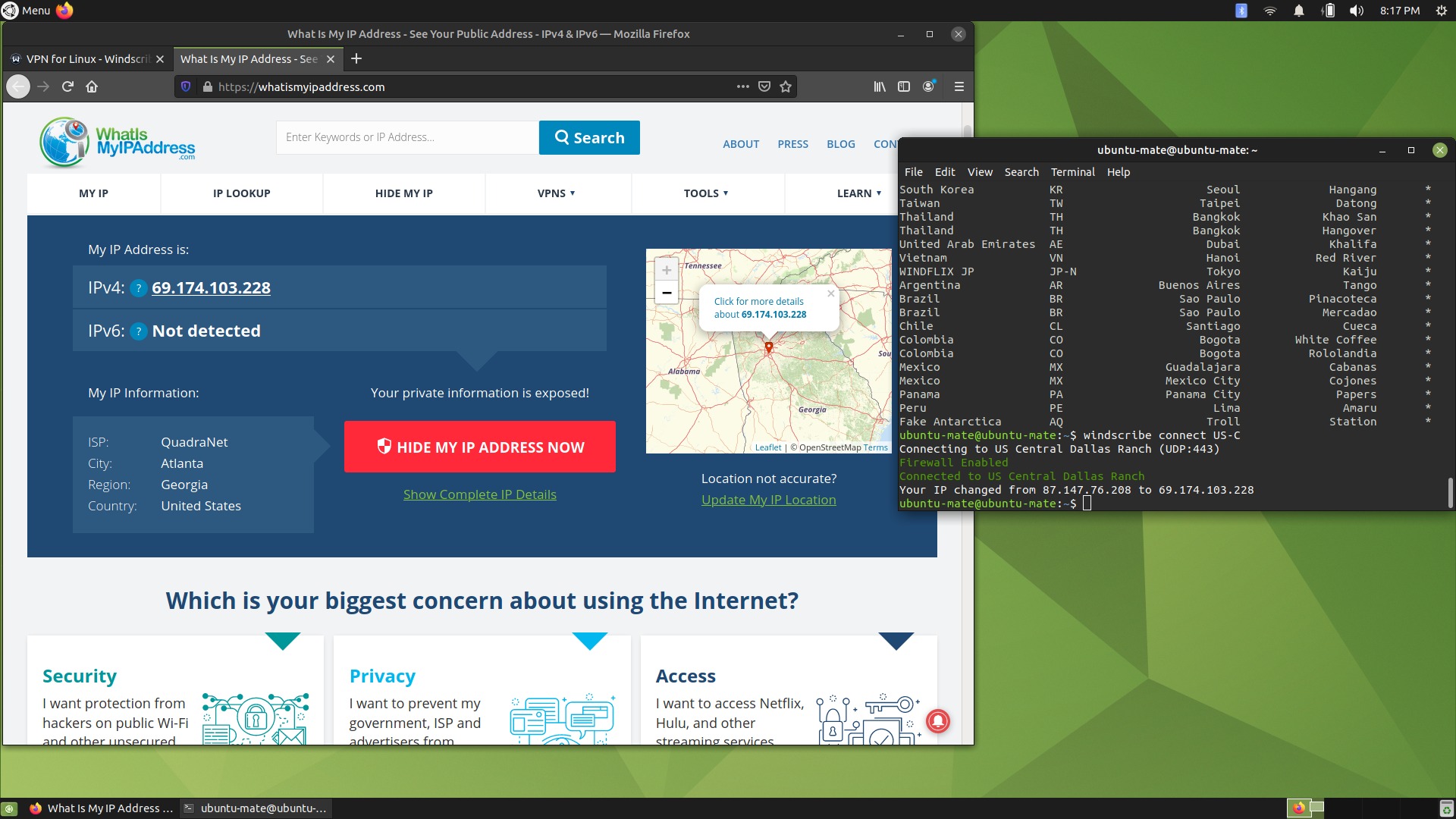
Note that “US-C” is for both Dallas and Atlanta, and while it said to have connected to Dallas, it actually connected to Atlanta.
Further reading for those who still don’t know why are they so keen to pay for a VPN subscription:
Do VPNs Actually Protect Your Privacy?
Luckily, most of us are not the target of active investigation by the NSA. As a result, for a number of threat models, a VPN might be a great tool to help you avoid snooping and spying by bad actors like an ISP, or your creepy neighbor. On the other hand, it’s always worth spending some time threat modeling to figure out what you’re trying to keep private, and from whom it must be kept private. VPNs aren’t a panacea, and using one might actually make you an easier target depending on your threat model.
Michal Špaček, a Web security guy: I don’t use any VPN for security or anonymity (and it mentions NordVPN!)
I don’t use any VPN (Virtual Private Network) for security. I don’t even use any VPN for anonymity. The VPN providers can’t guarantee one anyway, a VPN provider is just another Internet Service Provider. Having researched some “VPNs”, I can safely say that the VPN landscape has turned into a VPN minefield with pseudonymous companies leading the market, with some browser extensions redirecting to spam sites, while others don’t even encrypt the traffic.
Oh, he’s mean.
However, I use a VPN provider to bypass stupid geo restrictions, to check location-based pricing, to allow me to google for weird stuff without the rest of the devices on the same network getting CAPTCHA’d because of unusual bot-like queries. But I don’t use a VPN for staying safe online.
Toldya!
The content in this post does not apply to using VPN for their intended purpose; that is, as a virtual private (internal) network. It only applies to using it as a glorified proxy, which is what every third-party “VPN provider” does.
I had a similar disclaimer myself.
Why not?
Because a VPN in this sense is just a glorified proxy. The VPN provider can see all your traffic, and do with it what they want – including logging.But my provider doesn’t log!
There is no way for you to verify that, and of course this is what a malicious VPN provider would claim as well. In short: the only safe assumption is that every VPN provider logs.
And remember that it is in a VPN provider’s best interest to log their users – it lets them deflect blame to the customer, if they ever were to get into legal trouble. The $10/month that you’re paying for your VPN service doesn’t even pay for the lawyer’s coffee, so expect them to hand you over.But a provider would lose business if they did that!
I’ll believe that when HideMyAss goes out of business. They gave up their users years ago, and this was widely publicized. The reality is that most of their customers will either not care or not even be aware of it.But I pay anonymously, using Bitcoin/PaysafeCard/Cash/drugs!
Doesn’t matter. You’re still connecting to their service from your own IP, and they can log that.But I want more security!
VPNs don’t provide security. They are just a glorified proxy.But I want more privacy!
VPNs don’t provide privacy, with a few exceptions (detailed below). They are just a proxy. If somebody wants to tap your connection, they can still do so – they just have to do so at a different point (i.e. when your traffic leaves the VPN server).But I want more encryption!
Use SSL/TLS and HTTPS (for centralized services), or end-to-end encryption (for social or P2P applications). VPNs can’t magically encrypt your traffic – it’s simply not technically possible. If the endpoint expects plaintext, there is nothing you can do about that.
When using a VPN, the only encrypted part of the connection is from you to the VPN provider. From the VPN provider onwards, it is the same as it would have been without a VPN. And remember, the VPN provider can see and mess with all your traffic.
The last phrase is not entirely accurate. Also, what follows is not entirely something I agree with. Using a VPN “in a known-hostile network, e.g. a public airport WiFi access point,” is bullshit. What does it mean known-hostile? Watch again Tom Scott’s video! He can be annoying many times, but here he’s just right. Please do use a VPN, but make sure you know what you need it for!
But Yegor is after your money! The same guys from Windscribe offer this free DNS service:

I mean, this one, in the hope you’ll pay for more control over it, e.g. to unblock geo-restricted content (for which they’d probably use a proxy, so it’s not just a DNS, but the rest of the traffic is unaffected). This is not a VPN though, and it should not be used with a VPN!
As for the advantages of DoH and DoT, maybe some other time.

This being said, ExpressVPN for Android works great even on Huawei phones without Google Play Services.
I don’t trust either my VPN or my ISP. But my ISP knows FAR more about me, starting with real name and home postal address. So I want to hide as much as possible from my ISP (compartmentalization). So I use a VPN 24/365. Even if it turns out to be the most malicious VPN in the world, all it sees is HTTPS or Tor traffic, and I didn’t have to give my real name when I signed up for it. The damage the VPN could do to me is much less than the damage my ISP could do, because it has much less data about me to sell.
That said, a VPN is just one small positive tool to use, adding some encryption in certain places, hiding some data from my ISP, mixing my traffic with that of 100K other users using the same IP address from the same VPN server. And yes, it allows me to defeat geo-blocks and make it harder for someone to DMCA me.
So, I think the message should be “probably use a VPN, but know why, and know the limits of what it can do”.